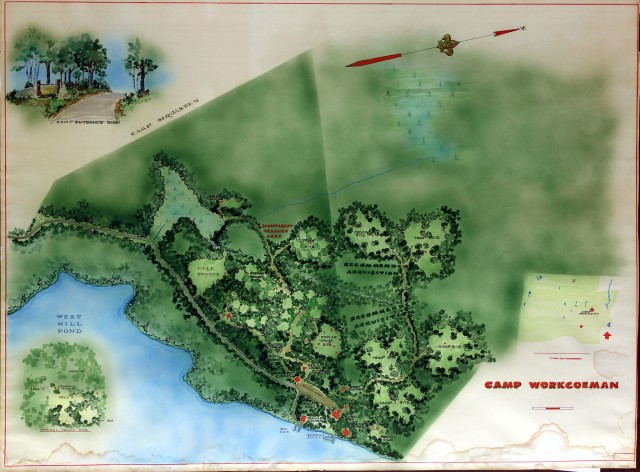
A few years ago, I wrote about a method of using a modified scanner to scan large documents in segments. While this led to high quality results, it is a very slow and tedious process. More recently, I’ve had a decently large number of maps and documents to digitize but didn’t care so much about the quality and had neither the time nor the patience to scan them using my previous method. Instead, I turned a small conference room into a very large makeshift camera stand. After removing a tile from the drop ceiling, a small wooden beam was placed on the ceiling grid, straddling the hole where the tile was removed. A DSLR camera was then attached to this beam, pointing straight down, with the camera tethered to a computer via USB. A table was placed under the camera. The document to be digitized was placed on the table, and a sheet of glass was placed on top of the document to keep it flat.1 The fluorescent tubes were removed from the closest ceiling light fixtures to remove glare from the glass; the same number of bulbs were removed from each side of the camera and table to keep the lighting consistent. Once everything was set up, documents were quickly photographed, with captures triggered using the computer. Once finished, lens distortion was removed from the images, and the images were cropped and level corrected. While the results weren’t nearly as nice as the scanner-based method, they were good enough for what I needed them for, and it was much, much faster. An example result is below.
Unfortunately, I neglected to photograph the camera set up.